MDM Isn’t Enough: Why You Still Need a Real Security Strategy
You’ve deployed Intune. Devices are enrolling, compliance policies are lighting up green, and someone’s gone full hero mode because Defender says your estate is “secure.”
Sorry to be that guy, but: MDM isn’t the endgame. It’s the start line!
In 2025, modern attackers don’t care about your BitLocker compliance. They’re jumping across cloud sessions, hijacking tokens, exploiting stale service accounts, and laughing at environments that think mobile device management equals a security strategy.
Let’s unpack why MDM on its own is dangerously incomplete — and what a real enterprise security posture should look like.
MDM: Great at Policy, Awful at Visibility
Intune and other MDM platforms (like JAMF, Workspace ONE, or MobileIron) are brilliant for configuration. They enforce device settings, deploy apps, and ensure a certain level of hygiene across your fleet. But what they don’t do is monitor, detect, or respond to threats.
They’re like a bouncer checking IDs at the door, but once someone’s inside, they’re not watching the room.
MDM can:
- Enforce encryption (BitLocker/FileVault)
- Require a PIN or biometric login
- Set compliance policies for OS version, AV, etc.
- Deploy apps and apply device restrictions
MDM can’t:
- Detect lateral movement or token replay
- Analyse cloud sign-ins and behavioural anomalies
- Prevent data exfiltration in real-time
- Intervene during an active attack
- Correlate endpoint and identity risk
If your estate is “secure” because Intune says it’s compliant, you’ve got a false sense of safety. And that’s worse than none at all.
Common MDM-Only Mistakes We Still See
1. Conditional Access with More Holes Than Swiss Cheese
Let’s say you’ve deployed CA policies – brilliant. But then come the exclusions:
-
“We’ll skip MFA for VIPs”
-
“This app doesn’t support modern auth, just allow it”
-
“Printers can’t do Conditional Access, so bypass them”
You’ve just created your own attack surface, piece by piece. Attackers love legacy – they’ll happily sidestep your security by abusing the same gaps you made for “convenience.”
2. Assuming Defender Antivirus Is the Same as Defender for Endpoint
Built-in AV? Great. But where’s your threat intel? Where’s the behavioural analysis? Where’s the 24/7 monitoring?
If you’re not backing MDM with Defender for Endpoint (Plan 2) or an equivalent EDR/XDR stack, you're blind to what’s happening after login.
3. Admins with Too Much Access, For Too Long
Let’s be crystal clear - A Global Admin in Entra ID (Azure AD) isn’t just a Microsoft 365 superuser — they’re a tenant god.
With the right API access, a Global Admin can:
-
Delete users, data, and services
-
Change or remove security policies
-
Modify Conditional Access rules
-
Reset other admins’ credentials
-
Delete your entire Azure subscription
Yes, really. If you’re integrated with Azure and using a CSP or enterprise subscription, GA rights extend across Microsoft 365 and Azure. One compromised GA account can lead to full platform loss, including compute, networking, identity, and storage.
So if you're handing out GA because someone “needs to make a mailbox,” you’re putting your entire estate on the line.
Security tip:
- Adopt a Least Privilege Model – Only assign the minimum permissions needed for the task. Most users don’t need GA. Most IT staff don’t either. Delegate roles like Exchange Admin or Security Reader instead.
- Use Privileged Identity Management (PIM) – Just-in-time access with approval, MFA, timeouts, and justification. No more standing admin rights.
- Separate Admin Accounts – Never allow daily-use accounts to have admin privileges. Admin accounts should be isolated and used only when required.
- Enforce MFA on All Admin Roles – And audit for any exclusions. MFA should be non-negotiable.
- Monitor Admin Sign-Ins – Set alerts on Global Admin activity, especially from new locations or devices.
- Review Access Regularly – Make it part of your quarterly checks. If someone doesn’t need GA anymore, revoke it.
In short: If one compromised login can delete your entire subscription… you don't have a secure environment.
4. Zero Control Over App Updates
Intune can deploy apps, sure. But who’s updating them? Your 500-user estate might be rocking:
-
Chrome v91
-
Java runtimes from 2016
-
12 versions of Zoom
Modern attacks are exploiting apps more than OS. If you’re not automating third-party patching with Intune Suite, Patch My PC, or Chocolatey, you're living on borrowed time.
What You Actually Need: A Layered Security Strategy
Security isn’t one tool. It’s an architecture. A mindset. A set of non-negotiables backed by automation, not best guesses.
Here’s what a real security stack for modern management looks like:
| Layer | Tooling Example | Purpose |
|---|---|---|
| MDM & Compliance | Intune, JAMF | Enforces baseline device hygiene |
| Access Control | Conditional Access, PIM | Ensures right access at the right time |
| Threat Detection | Defender XDR, Sentinel, Splunk | Detects, analyses, and correlates suspicious activity |
| Identity Protection | Entra ID Protection | Flags risky users, impossible travel, sign-in anomalies |
| App Management | Patch My PC, Intune Suite, Chocolatey | Keeps apps secure and updated |
| Data Protection | TLS 1.2/1.3, Purview DLP | Protects data in transit and at rest |
This isn't just "nice to have" anymore. With hybrid work, BYOD, and cloud services everywhere, your devices are exposed all the time.
But What About BitLocker PINs and BIOS Lockdown?
Let’s have the honest conversation: BitLocker PINs sound good on paper, but in practice, they’re a user - hostile security placebo.
Sure, they add an extra hurdle at boot — but let’s be real: most of your threats aren’t sitting in car parks with a crowbar and 30 minutes to brute-force a laptop. And if they are? A six-digit PIN isn't stopping them.
What a BitLocker PIN actually does:
- Slows down boot time and frustrates users (especially in policing, healthcare, or emergency services).
- Adds support overhead when someone forgets it at 5am.
- Gives a false sense of protection against physical threats.
And what it doesn’t do:
- Prevent nation-state or skilled attackers with physical access from getting in.
- Stop firmware-level attacks, bus sniffing, or TPM-side exploits.
- Protect against 99% of real-world threats — like phishing, token theft, or lateral movement.
If you’re relying on a boot PIN for security, you’re fighting yesteryear’s threats. Most data theft today isn’t someone stealing a laptop – it’s someone phishing credentials and logging in with full access.
What Actually Works?
Modern endpoint security is built on layers — not PINs. Here’s what actually protects your users and estate:
- UEFI Secure Boot to block bootkits.
- TPM 2.0 with BitLocker.
- Code Integrity + VBS + HVCI to enforce secure kernel operations.
- Zero trust enforcement via Intune compliance and Conditional Access.
- FIDO2 key-based auth to kill off password-based logins entirely.
- Privileged Access Workstations (PAWs) for admins — no standing access.
- TLS 1.2/1.3 and SSL everywhere for data in transit.
This is what actually holds up under scrutiny — even if your adversary isn't a petty thief, but a nation-state with time, tools, and talent.
Your posture should prevent logical access, not just physical.
Final Thoughts: If Intune Says You're Compliant, Are You Actually Secure?
That green tick might feel good. But it doesn’t mean you’re protected.
- Compliance ≠ Protection
- MDM ≠ Monitoring
- Access ≠ Identity validation
- Config ≠ Threat detection
Real security is layered, automated, and assumed breached until proven otherwise. If you’ve deployed Intune, great. Now back it with Conditional Access, EDR, automated patching, and identity threat detection.
Because when the breach happens — and it will — you don’t want to be the one saying “but we had Intune.”
Further Reading / Sources:
Need help pulling this together in your organisation?
Drop me a line. Or better yet — review your Conditional Access exclusions before someone else does.
Windows 10 Is Out, Windows 11 Is In: Why It’s Time to Upgrade
January 21, 2025BlogIntune,Windows11
The clock is ticking for Windows 10. Microsoft has officially marked October 14, 2025, as the end-of-life date for the beloved OS. That might sound like a distant deadline, but in IT terms, it’s right around the corner. If your organization hasn’t started planning for Windows 11, now’s the time to get moving.
Let’s talk about what end-of-life means, why you can’t ignore it, and how to make the jump to Windows 11 without losing your mind (or your weekends).
What Does End-of-Life Mean for Windows 10?
When Windows 10 hits its expiration date, here’s what you’ll lose:
- No more security updates: Vulnerabilities won’t get patched, leaving your systems exposed.
- No feature updates: Windows 10 will stagnate while the rest of the tech world moves forward.
- No official support: You’re on your own for troubleshooting and compliance issues.
Running an unsupported OS isn’t just risky—it’s a compliance and security nightmare. For most businesses, staying on Windows 10 past 2025 simply isn’t an option.
Why Upgrade to Windows 11?
Windows 11 isn’t just a cosmetic refresh. It’s built for the modern workplace, focusing on security, productivity, and future-proofing. Here’s why it’s worth the move:
- Zero Trust Security: Features like TPM 2.0, Virtualization-Based Security (VBS), and hardware root-of-trust support make it a fortress for modern threats.
- Productivity Enhancements: Snap Layouts, better multi-monitor support, and Teams integration help users work smarter, not harder.
- Hybrid Work Ready: Optimized for cloud environments, Windows 11 is built with hybrid and remote work in mind.
- Long-Term Support: Sticking with Windows 10 means falling further behind, while Windows 11 positions your organization for what’s next.
Planning Your Windows 11 Upgrade
The move to Windows 11 doesn’t have to be chaotic. Here’s a step-by-step approach to keep things smooth:
1. Assess Your Hardware
Windows 11 has stricter requirements than its predecessor (hello, TPM 2.0). Start by auditing your current hardware to see what’s compatible.
Use Intune for a Hardware Assessment
- Navigate to Endpoint Analytics in Intune.
- Check the Work From Anywhere report to identify devices that are Windows 11 ready.
Tip: Devices that don’t meet the requirements may need upgrading or replacing—start budgeting early.
2. Test the New OS
Don’t roll out Windows 11 to everyone at once. Test it with a small group of users first (preferably IT and power users). Use their feedback to refine your deployment strategy.
3. Leverage Intune for Deployment
If you’re managing your environment with Intune, upgrading to Windows 11 is straightforward. Use Windows Update for Business to deploy feature updates in a controlled manner:
- Go to Devices > Windows > Feature Updates.
- Create a new policy targeting Windows 11 24H2 or the latest version.
- Assign the policy to Azure AD groups.
Pro Tip: Use Update Rings to stagger the rollout and test updates before pushing them to all users.
4. Train Your Users
Even minor interface changes can confuse users. Prepare your teams with:
- Short training sessions on Windows 11’s new features.
- Guides or videos highlighting productivity boosters like Snap Layouts and Teams integration.
Overcoming Common Objections
Some users (or even IT admins) might resist the change. Here’s how to address the usual pushback:
- “We need to test everything before upgrading.”
Sure, but Windows 11 is part of an evergreen model—updates will keep coming. Adopt a test-and-deploy mindset instead of waiting for “perfect.” - “Our hardware isn’t ready.”
Start identifying devices that need replacing now. You’ve got time, but don’t leave it too late. - “We can’t afford downtime.”
Use Intune’s zero-touch deployment capabilities and tools like Windows Autopilot to minimize disruption.
Why Procrastination Is a Bad Idea
October 2025 might seem far away, but large-scale migrations take time. If you wait until 2025 to start planning, you’ll be scrambling to meet the deadline. Here’s why early action is critical:
- Avoid the rush: As the deadline approaches, vendors and support teams will be swamped.
- Stay secure: Upgrading sooner means fewer months spent on an unsupported OS.
- Get ahead of the curve: Windows 11’s modern tools and features can drive productivity gains right now.
Final Thoughts
The end of Windows 10 isn’t just a deadline—it’s an opportunity. Moving to Windows 11 brings better security, improved productivity, and a platform built for the future of work. With tools like Intune and Windows Autopilot, the upgrade process can be streamlined and efficient.
So, don’t wait. Start planning your move today, and by the time October 2025 rolls around, you’ll already be reaping the benefits of Windows 11.
Ready to Get Started?
Let me know how I can help you make your Windows 11 upgrade seamless and stress-free!
Windows 11 Hotpatching: Because Nobody Likes Reboots
December 15, 2024BlogWindows11,24H2
Patch Tuesday just got a whole lot less painful. With Hotpatching, Microsoft is bringing a server-grade feature to Windows 11 Enterprise, letting you install security updates without the dreaded reboot. Think of instant protection, no downtime, and fewer interruptions for your users. Sound too good to be true? Let’s break it down.
What is Hotpatching?
"Hotpatching" is all about applying security updates directly to in-memory processes—no reboot required. It’s been around in Windows Server for a while, but now it’s making its way to Windows 11 Enterprise (version 24H2).
Here’s how it works:
- Updates are applied immediately to running processes.
- No restart means users can carry on working without disruption.
- Your systems stay protected with near-zero downtime.
It’s a win for productivity and IT sanity alike.
Why Does Hotpatching Matter?
Traditional updates usually require a reboot, which means:
- Interrupting users mid-task (cue angry emails).
- Scheduling downtime for critical systems.
- Delayed patching, leaving vulnerabilities exposed longer.
Hotpatching flips the script. Here’s why it’s a game-changer:
- Instant protection: Updates take effect as soon as they’re applied.
- No downtime: Systems stay up and running—no user complaints about “another restart.”
- Fewer reboots overall: Microsoft reduces the yearly reboot count from 12 (monthly) to just 4 (quarterly).
How Does It Work?
Hotpatching follows a simple quarterly update cycle:
1. Quarterly Baseline Updates: At the start of each quarter, a cumulative update installs the latest features and security patches. This one does require a reboot, but only four times a year.
2. Monthly Hotpatch Updates: For the next two months, hotpatches deliver security fixes without restarting the system.
This streamlined process means fewer interruptions for your users and faster adoption of critical security updates.
Getting Started with Hotpatching
To take advantage of Hotpatching, here’s what you’ll need:
- Windows 11 Enterprise (24H2 or later): Build 26100.2033 or above is required.
- Microsoft Intune: For managing update policies.
- Licensing: Windows Enterprise E3 or E5 subscription.
How to Enable Hotpatching in Intune
Setting up Hotpatching is straightforward:
1.Log into Intune:
- Head to the Microsoft Endpoint Manager admin center.
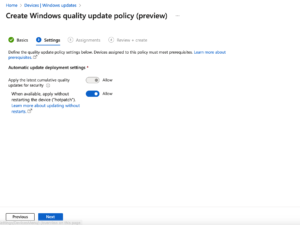
2.Create a New Update Policy:
- Navigate to Devices > Windows > Update rings for Windows 10 and later.
- Click + Create Windows quality update policy (preview).
- Configure the policy to enable Hotpatching.
3.Assign the Policy:
- Target specific device groups for the update ring.
4.Monitor Compliance:
- Use Intune’s Update Compliance Reports to track which devices are up to date and identify any issues.
When Should You Use Hotpatching?
Hotpatching is perfect for organizations that can’t afford downtime but still need to stay secure. Key use cases include:
- Enterprise Desktops: Keep users productive without disruption.
- Healthcare and Finance: High-availability environments where downtime isn’t an option.
- Critical Systems: Protect machines immediately without scheduling reboots.
Limitations to Keep in Mind
While Hotpatching is a massive improvement, it’s not a magic bullet:
- It’s only available for Windows 11 Enterprise (sorry, Pro users).
- Major feature updates and some patches still require reboots (but far fewer).
Final Thoughts: Updates Made Easier
Hotpatching is a breath of fresh air for IT teams juggling user productivity and system security. By applying updates without restarts, you get the best of both worlds: up-to-date systems and happy end-users.
If you’re running Windows 11 Enterprise, now’s the time to embrace this feature. Set up your policies, roll it out, and say goodbye to the endless cycle of reboots. Hotpatching is here to make your life easier—use it!
What’s Next?
Got questions about setting up Hotpatching or managing updates? Let me know—I’m here to help.
Let’s keep those systems secure and running.
Intune Done Right: Wrangling App Chaos, One Update at a Time
Managing applications across a diverse set of devices has always been a challenge, especially in enterprise environments. With Intune, you’ve got a powerful toolset for app deployment, version control, and automated updates. But Intune alone has its limits—especially when it comes to updating third-party apps and managing large app libraries. Here’s how to optimize your application management strategy in Intune, where supersedence and third-party tools like Microsoft Intune Suite, Chocolatey, and Patch My PC can help make app management smooth, scalable, and headache-free.
1. Choose the Right Deployment Strategy for Your Apps
Intune offers several deployment methods, allowing you to tailor delivery to different app types and user needs. However, one pitfall to avoid is making all apps required. While Intune does handle dependencies well, it installs required apps in a random order, meaning it has no concept of which apps are most important to the user.
Imagine a user with 15 required apps. They could be left waiting for the specific app they need to complete a task while other, less critical apps install first. This unpredictable order can lead to user frustration, wasted time, and unnecessary IT support requests.
To sidestep these issues, consider deploying only essential apps as required and using Available for Install for non-critical apps that users can download as needed from the Company Portal. This approach allows users to access important apps immediately, without waiting for the entire set to install.
- Available for Install: Perfect for optional applications that users can download as needed through the Company Portal.
- Required Install: Ensures that essential apps are deployed automatically to all targeted devices or groups, with no user intervention required. Ensure that only the most essential apps are "required"
- Uninstall: Quickly removes apps from specified devices, helping you maintain compliance or remove outdated versions easily.
Selecting the right deployment type based on your app’s function and necessity allows you to give users the flexibility they need while ensuring critical applications are always up-to-date.
2. Simplify App Version Control with Supersedence—But Beware the Manual Workload
Intune’s supersedence feature is a useful tool for updating Win32 applications when you’re managing apps through Intune alone. Supersedence lets you specify that a new version of an app replaces an older one, automatically removing outdated versions across your environment. This is especially valuable for controlling Microsoft applications and Win32 apps, helping to keep app versions consistent.
However, supersedence relies on manually packaging and updating each application—an enormous workload if you’re managing a large app library. Imagine you’re handling 500 apps, each requiring manual packaging and configuration updates with each new version. Without automation, supersedence can become a bottleneck in maintaining an evergreen environment. Here’s where tools like Microsoft Intune Suite, Chocolatey, and Patch My PC shine.
3. Filling the Gaps: Intune Suite, Chocolatey, and Patch My PC
If your app library is extensive, you need more than just supersedence to keep applications current. Microsoft Intune Suite, Chocolatey, and Patch My PC offer automation and streamlined packaging capabilities, making large-scale app management far easier. Here’s a breakdown:
- Microsoft Intune Suite: Expanding on Intune’s core capabilities, Intune Suite provides enhanced automation, security, and management features. Its app management capabilities offer deeper support for automating updates, no packaging, and enhancing visibility, allowing IT to manage large app portfolios more effectively without the manual work required by supersedence.
- Chocolatey: This package manager simplifies the deployment, updating, and removal of third-party applications and integrates well with Intune. Chocolatey automates the packaging and updating process for a wide range of applications, eliminating the manual steps required with supersedence alone.
- Patch My PC: Specifically designed for third-party app patching, Patch My PC integrates seamlessly with Intune to provide automated updates for a wide array of third-party apps. With robust reporting, version control, and auto-update capabilities, Patch My PC ensures your app library stays evergreen without constant manual intervention. This tool is especially valuable for large app libraries, allowing IT teams to automate patching and package updates with ease.
Using one of these tools alongside Intune reduces the manual work involved in packaging, deploying, and updating apps across a large enterprise, helping you maintain an up-to-date, secure app ecosystem with minimal hands-on effort, yes they come at a cost but that is offset in far reduced effort and complexity.
4. Streamline App and OS Updates with Windows Autopatch for a Fully Evergreen Environment
Modern management isn’t just about deploying applications—it’s about keeping everything, from apps to the operating system, up-to-date in a secure, evergreen state. Windows Autopatch, available as part of Intune, takes OS updating a step further by automating Windows updates across your organization. Unlike WUfB, Autopatch is a fully managed service that handles Windows quality and feature updates on your behalf, freeing up IT resources and ensuring a consistent, optimized update process.
When paired with third-party tools like Patch My PC and Chocolatey to automate updates for non-Microsoft applications, Autopatch enables a comprehensive, evergreen environment. This integrated approach ensures all software stays secure and current without manual effort, providing a seamless experience for end-users and a more resilient setup for IT.
5. Provide Flexible, Self-Service Options for User Empowerment
Users often need quick access to certain apps that may not be “required” for everyone. Intune’s Company Portal allows you to publish optional apps, giving users the freedom to install what they need, when they need it. By using this self-service model, you enable users to install optional apps or essential updates immediately without relying on IT.
This self-service approach is especially useful when updates are rolled out across the organization. Users can check the portal for the latest versions or download optional tools as their needs evolve. The flexibility to access apps on-demand improves user satisfaction, cuts down on IT support requests, and provides a more agile, responsive experience.
Wrapping Up: Optimizing App Management with Intune
When used to its full potential, Intune streamlines app deployment, updates, and management in ways that meet the needs of modern enterprises. From automated updates and lifecycle management to custom configurations and proactive monitoring, Intune enables your organization to stay flexible, secure, and ready to support user productivity.
However, for large app libraries, relying on Intune alone (and supersedence) for updates can lead to a high manual workload. Third-party tools like Microsoft Intune Suite, Chocolatey, and Patch My PC take Intune’s capabilities to the next level by automating patching, packaging, and updating processes that would otherwise require extensive hands-on effort. By combining Intune with specialized tools, you’re setting up your organization for smoother, more efficient app management that meets the demands of today’s dynamic, evergreen IT environment.
Intune Done Right: Business Change or Bust!
November 29, 2024BlogIntune,Modern Management,Business Change
Adopting modern management tools like Intune, Azure AD, and other MDM solutions is a strategic move for any enterprise aiming to boost flexibility, security, and efficiency. But here’s the hard truth: rolling out these tools without a business change strategy is a recipe for failure. For medium and large organizations especially, aligning processes, people, and strategy with modern management is critical. Without it, you risk poor adoption, endless troubleshooting, and missed opportunities—especially in an evergreen IT environment where Windows, applications, and security policies are constantly evolving. Here’s why business change is non-negotiable for a successful modern management rollout in any enterprise.
1. Modern Management Requires Enterprise-Wide Process Changes
Modern management tools are agile, cloud-based, and highly adaptable, but they require different workflows than traditional on-prem setups. Moving from Active Directory and SCCM to a cloud-centric approach means changing how teams work and how IT supports the business. Without adjusting enterprise processes, you’re slapping modern tools onto an outdated system, leading to mismatched policies, broken workflows, and frustration for both IT and end-users.
Key Insight: Align business change processes with the mobile, flexible nature of modern management, making it easier for departments across the enterprise to adopt the new system smoothly.
2. Evergreen IT Demands Continuous Change—and Enterprises Must Be Ready
Modern management in a large enterprise isn’t just a one-time deployment; it’s a continuously evolving approach. With evergreen IT, regular updates roll out across tools, OS versions, and applications, meaning your entire organization must adapt without significant disruption. A lack of business change strategy leaves each update feeling like a shock rather than a smooth transition, causing disruption for users and backlogs for IT.
One major shift is the continuous updates in Windows and business applications. Gone are the days when organizations could delay updates indefinitely to allow time for extensive testing. With Windows updating regularly, business-as-usual (BAU) applications must be updated to stay compatible, raising the question: who’s managing that work?
The days of waiting for IT to test every patch before rollout are over, and businesses need to adjust. Without clear ownership of application updates, your organization could face compatibility issues, security risks, and degraded user experiences.
Key Insight: Embrace a mindset of continuous improvement, treating each update as a strategic opportunity for refinement rather than a hurdle. For large organizations, this approach minimizes user downtime and keeps systems performing at peak.
3. End-User Training and Communication Are Non-Negotiable
Rolling out modern management tools to thousands of users without a clear training and communication plan is a recipe for failure. Large organizations need structured, consistent training programs to help users understand new interfaces, settings, and behaviors.
Without this, confusion reigns—user productivity drops, support calls rise, and adoption lags.
Key Insight: Design a training and communication strategy that scales across teams and departments, empowering employees with the skills they need to maximize productivity.
4. Security is Dynamic—So Should Be Your Enterprise Policies
Modern management often means implementing dynamic security policies—conditional access, compliance checks, and real-time threat detection.
However, these tools are only as effective as the processes that govern them. Large enterprises, with their complex security requirements, need security policies that are adaptable and enforceable across varied departments and geographies.
Relying on static security policies tied to on-prem practices limits the benefits of dynamic cloud tools.
Key Insight: Develop adaptive security policies that can scale and respond quickly to emerging threats across your entire organization, ensuring each department stays secure without losing productivity.
5. IT and Support Teams Need to Evolve Alongside the Technology
For large enterprises, modern management doesn’t just change device management—it reshapes the whole IT support model.
Legacy setups often include centrally managed, on-prem solutions that differ vastly from cloud-based support and remote troubleshooting required by modern management. Without upskilling and evolving the support team, your enterprise risks service delays, inconsistent issue resolution, and missed opportunities to proactively manage the environment.
Key Insight: Invest in IT and support training to ensure teams are skilled in cloud management, remote troubleshooting, and proactive monitoring. This prepares your IT team for the challenges of large-scale modern management.
6. The Culture Shift: Empowering Users While Maintaining Control
One of the biggest challenges for medium and large enterprises is balancing user empowerment with control.
Modern management encourages a flexible, user-centric approach, but without the right cultural shift, users may find themselves confused by new expectations or bypassing policies altogether.
Large organizations, with their diverse teams and departmental needs, must create a culture that supports user independence while enforcing security and compliance.
Key Insight: Establish a culture of trust and accountability, making it clear that while users have greater flexibility, security remains paramount.
7. Prevent Fragmentation and Shadow IT
In large enterprises, the temptation to rely on unapproved tools grows when official systems aren’t meeting user needs.
A lack of business alignment in modern management can result in fragmentation and shadow IT, where departments find their own solutions to work around limitations. This not only compromises security but also creates data silos and increases IT complexity.
Key Insight: Engage department heads and team leads in the rollout process to ensure the tools and processes meet diverse needs, keeping teams unified and reducing shadow IT.
Wrapping Up: Modern Management Without Business Change is a Missed Opportunity
For medium and large enterprises, implementing modern management without business alignment is like upgrading to a high-performance engine without adjusting the rest of the car—it’s bound to underperform.
In an evergreen IT world, where change is constant, your organization must be ready to adapt seamlessly.
With a strong business change strategy, you’re not just adopting new tools; you’re building a resilient, user-centered, and flexible IT framework ready to meet the demands of a modern, dynamic enterprise.
Ignite 2024: The Innovations You Need to Know (And Why They Matter)
Microsoft’s Ignite 2024 conference has wrapped up, and this year’s theme was clear: AI everywhere, hybrid cloud domination, and making tech simpler for everyone. With announcements spanning new hardware, productivity tools, and AI-powered upgrades, here’s your no-nonsense roundup of the highlights that actually matter.
1. Autonomous AI Agents: Automating the Tedious Stuff
Microsoft unveiled autonomous AI agents—tools designed to handle complex, repetitive processes like customer returns or invoice management. These agents act without human oversight, making them ideal for streamlining business workflows.
Why it matters: This isn’t just about saving time; it’s about giving teams back their bandwidth to focus on more impactful work. If you’ve got repetitive processes eating up hours, AI might be your new best friend.
https://blogs.microsoft.com/blog/2024/10/21/new-autonomous-agents-scale-your-team-like-never-before/
2. Windows 365 Link: Cloud PCs Made Physical
 Say hello to the Windows 365 Link, Microsoft’s new compact device designed to connect users directly to their Windows 365 Cloud PCs. Priced at $349, it supports dual 4K monitors, Wi-Fi 6E, and Bluetooth 5.3, offering a portable solution for hybrid workforces or hot-desking setups.
Say hello to the Windows 365 Link, Microsoft’s new compact device designed to connect users directly to their Windows 365 Cloud PCs. Priced at $349, it supports dual 4K monitors, Wi-Fi 6E, and Bluetooth 5.3, offering a portable solution for hybrid workforces or hot-desking setups.
Why it matters: This isn’t just another device—it’s a step toward fully portable workspaces that don’t rely on traditional laptops. If you’re managing hybrid teams, this could simplify setups and boost flexibility.
3. Taskbar Productivity Boosts in Windows 11
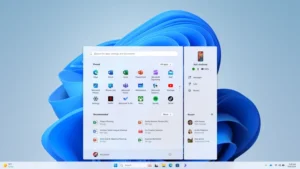 Microsoft is bringing Microsoft 365 Companions to the Windows 11 taskbar. This upgrade integrates contacts, files, and calendar appointments directly into your taskbar, giving users faster access to key tools.
Microsoft is bringing Microsoft 365 Companions to the Windows 11 taskbar. This upgrade integrates contacts, files, and calendar appointments directly into your taskbar, giving users faster access to key tools.
Why it matters: It’s a small change with big implications for productivity. By keeping everything you need one click away, it reduces the cognitive load of switching between apps.
4. Custom Chips for AI and Security
Microsoft announced two custom-designed data center chips, aimed at accelerating AI workloads and boosting data security. These chips are tailored for hyperscale environments, reducing reliance on third-party processors.
Why it matters: With AI demand skyrocketing, these chips ensure Microsoft has the infrastructure to support faster, more secure cloud applications. For enterprises running intensive AI models, this could mean a big performance boost.
https://news.microsoft.com/source/features/ai/in-house-chips-silicon-to-service-to-meet-ai-demand/
5. Copilot Actions: Automating Admin Work
Microsoft 365 Copilot got a handy upgrade with Copilot Actions, a feature designed to automate tedious tasks like summarizing meeting notes or generating reports.
Why it matters: Admin tasks are a drain on productivity. Copilot Actions promises to take that load off your plate, letting you focus on actual work instead of housekeeping.
Why This Ignite Matters
Microsoft’s announcements aren’t just shiny new toys—they’re signals of where the industry is headed. From AI taking over mundane tasks to hardware that makes hybrid work seamless, Ignite 2024 was about one thing: making technology work smarter, not harder.
Final Thoughts
Whether you’re excited about AI’s growing role, the Cloud PC revolution, or custom silicon reshaping data centers, one thing’s for sure: Microsoft is pushing hard to integrate their ecosystem into every aspect of modern business.
Which Ignite 2024 highlight stands out to you? Let’s talk about how these innovations could impact your tech strategy.
Windows 365 Link: Cloud PC Just Got Real
November 19, 2024BlogIntune,Windows365
We’re all used to the idea of a PC being a device—your laptop, your desktop, maybe even a fancy all-in-one. But what if your "PC" wasn’t really a PC at all? Enter the Windows 365 Link, Microsoft’s compact bridge between you and the cloud. It’s not here to replace your hardware entirely, but to rethink how we use it.
The Link is designed to connect directly to your Windows 365 Cloud PC, making your workspace portable, secure, and—most importantly—not tied to a traditional endpoint. Let’s break down what this means for how we work and why it might be a big deal for businesses. It’s a rethink of how we approach security, management, and productivity. It also closes the missing gap that was present in the W365 ecosystem.

No Physical Attack Surface, No Problem
One of the Link’s standout features is its complete lack of local storage. No files, no apps, no admin accounts. At first, that might seem limiting, but here’s the genius: there’s nothing on the device for attackers to exploit. If the Link is stolen, it’s just a tiny paperweight for anyone who doesn’t have access to your Cloud PC.
For businesses handling sensitive data, like finance or healthcare, this is a game-changer. Local machines are always at risk of being breached or compromised. The Link removes that risk entirely by keeping everything in the cloud. It’s like a secure tunnel that ensures your data is always protected, no matter where you are.
- Physical theft: Lose a laptop, and your data could end up anywhere. Lose the Link? There’s nothing stored locally for attackers to exploit.
- Malware attacks: The locked-down OS prevents unauthorized software from running or installing locally, drastically reducing the risk of breaches.
- Privileged escalations: No local admin accounts mean attackers can’t exploit traditional elevation-of-privilege attacks to gain control.
For industries that deal with sensitive information—finance, healthcare, or government—the reduced attack surface makes the Windows 365 Link an obvious choice.
Built for Privileged Access Workstations (PAWs)
If you’ve ever tried to implement Privileged Access Workstations (PAWs), you know they’re a hassle. These specialized devices are designed for highly secure tasks—think system administration or managing sensitive data—but they’re costly and complex to set up. The Windows 365 Link changes that.
With no local data and built-in support for FIDO2 security keys, the Link makes securing privileged access much simpler. Passwordless, hardware-backed authentication means no weak passwords to exploit, and no need for bulky, high-spec machines just for security’s sake. At $349, it’s a cost-effective way to deploy secure workstations without sacrificing functionality. For IT admins, it’s a quick win that checks all the compliance boxes without breaking the budget.
- Secure by design: With no local admin accounts or storage, the Link aligns perfectly with the zero-trust principles of PAWs.
- Enhanced authentication: The device supports FIDO2 security keys, enabling passwordless, hardware-backed authentication for privileged users. This reduces the risk of phishing attacks and ensures only authorized personnel can access sensitive systems.
- Cost-effective: At $349, it’s significantly cheaper than building out dedicated, high-end PAW setups while offering superior security through cloud-native management.
Built for Hybrid Work
Perfect for the Hybrid Work Era
Hybrid work isn’t a trend anymore—it’s the way we work now. But with hybrid setups come challenges: laptops lugged between home and office, forgotten chargers, and inconsistent environments. The Link offers a simple solution.

It’s small, portable, and packed with modern connectivity. Dual 4K monitor support, Wi-Fi 6E, Bluetooth 5.3, and Ethernet mean it’s ready for just about any setup. Plug it into a monitor and peripherals, and you’re instantly connected to your Cloud PC. No need to sync files or carry around a full device.
This isn’t just handy for hybrid workers—it’s perfect for hot-desking environments, too. Instead of provisioning expensive laptops for every desk, you just provide a Link. Simple, scalable, and far less hassle for IT.
- Dual 4K monitor support for high-productivity setups.
- Wi-Fi 6E, Bluetooth 5.3, and Ethernet connectivity to ensure compatibility with any network.
- Plug-and-play simplicity that turns any screen into a secure workstation connected to your Cloud PC.
IT Management Without the Drama
If you’re an IT admin, you’ve probably rolled your eyes at “revolutionary” devices that make big promises but add complexity to your workload. The Link is different because it’s built to integrate seamlessly into the tools you’re already using, like Microsoft Intune.
From zero-touch provisioning to automatic updates, managing the Link is as straightforward as managing a traditional endpoint. Policies? Same as any other device. Updates? They’re applied in the background overnight. It’s an endpoint that fits neatly into your existing processes without reinventing the wheel.
And because it’s entirely cloud-driven, there’s no need to worry about patching local vulnerabilities, maintaining a separate device inventory for physical machines or even having these on your internal facing LAN. It just works.
Why It Matters
The Windows 365 Link might look like a small, unassuming device, but it’s tackling some big problems. It removes local vulnerabilities, simplifies endpoint management, and makes hybrid work more efficient. For businesses already using Windows 365, it’s an obvious next step. For those on the fence about cloud PCs, it might just be the nudge they need.
This isn’t about replacing every device in your organization, but about rethinking how and where you work. The Link isn’t flashy, and it doesn’t need to be. It’s about utility—making your workspace more secure, more portable, and less of a headache for everyone involved.
Final Thoughts
The Windows 365 Link isn’t going to revolutionize how you work overnight. But it’s a clear step toward a world where your "PC" isn’t tied to a physical machine. It’s secure, simple, and built for modern work.
If you’re managing hybrid teams, privileged users, or just looking to simplify your endpoint strategy, this little device is worth a closer look. It’s not the whole solution, but it might just be the most practical piece of the puzzle you’ve been missing.
Modern Management on an Old Network? Good Luck with That!
Shifting to modern management tools like Intune, VMware Workspace ONE, MobileIron, and Azure AD is a big step forward for any organization. These cloud-first tools are designed to simplify device management, boost security, and support today’s mobile workforce. But here’s the reality: if you’re running them on an outdated network, you’re setting yourself up for constant headaches. Moving away from traditional Active Directory (AD) and SCCM to modern MDM and cloud management requires a network built for speed, flexibility, and security. Keeping your legacy network design not only limits performance but holds back the benefits of cloud-managed solutions, Conditional Access, and productivity tools like Microsoft 365. Here’s why upgrading your network is a must for getting the most out of your modern management setup.
1. Avoid Network Bottlenecks: Direct Internet Access is Essential
Old networks are built around the corporate data center, often relying on force-tunneled VPNs that route all traffic through a single site. This approach made sense for on-prem resources but creates huge bottlenecks when accessing cloud services. For tools like Intune and Microsoft 365 to function properly, devices need direct internet access to reach cloud resources without being slowed down by outdated routing. Keeping everything tied to the data center hinders speed, and users will notice the impact on productivity apps like Microsoft Teams.
2. Move Beyond Perimeter-Based Security
Traditional network security was built on the idea of a physical perimeter—keeping threats out by securing the edges of the network. But with cloud-managed devices and remote work, there’s no single “edge” to protect. Instead, modern management relies on a Zero Trust model, where each access request is verified independently based on factors like location, device compliance, and risk level. Tools like Conditional Access in Azure AD allow you to control access dynamically, but they require a network built to handle flexible security policies, not rigid perimeter defenses.
3. Optimize Network Access with SASE and Split-Tunneling VPNs
The new era of mobile and cloud-based work needs network solutions that are just as modern. Secure Access Service Edge (SASE) and split-tunneling VPNs offer a solution by enabling direct access to the internet for cloud services, while routing only sensitive traffic through the corporate network. SASE combines networking and security in the cloud, giving you the performance of direct internet access with essential security controls. Split-tunneling VPNs, meanwhile, allow cloud-bound traffic to bypass the VPN, reducing latency and allowing management tools to work as designed.
https://www.microsoft.com/en-gb/security/business/security-101/what-is-sase
4. Embrace Resiliency with a Cloud-First Network Design
 Modern management tools like Intune and Azure AD minimize reliance on local infrastructure by keeping identities, policies, and data in the cloud. But to take full advantage of this, you need a network that can match that resilience. Traditional networks tied to data centers and VPNs are vulnerable to on-prem disruptions. By designing your network with cloud-first principles, you can keep users connected to resources like Microsoft 365, even if there’s an issue with the physical site. Cloud-first networks reduce downtime, support mobile users, and ensure business continuity.
Modern management tools like Intune and Azure AD minimize reliance on local infrastructure by keeping identities, policies, and data in the cloud. But to take full advantage of this, you need a network that can match that resilience. Traditional networks tied to data centers and VPNs are vulnerable to on-prem disruptions. By designing your network with cloud-first principles, you can keep users connected to resources like Microsoft 365, even if there’s an issue with the physical site. Cloud-first networks reduce downtime, support mobile users, and ensure business continuity.
5. A Modern Network Enables Real Productivity Gains
Ultimately, upgrading your network to support modern management doesn’t just benefit IT—it enhances productivity across your organization. Tools like Microsoft Teams, OneDrive, and SharePoint are core to collaboration, and they perform best on networks that allow for direct, low-latency access. A network built for the cloud keeps users connected, reduces frustrating delays, and lets modern management tools support users wherever they are, without the constraints of outdated infrastructure.
The Bottom Line: A Modern Network for a Modern Workforce
Transitioning to Intune, Azure AD, and other cloud-based management tools is only half the journey. To fully unlock the benefits of these solutions, your network needs to keep up. By rethinking network design with direct internet access, Zero Trust, and cloud-first resilience, you’re setting your organization up for the productivity, flexibility, and security that today’s workforce demands.
Intune Done Right: Why Fresh Beats Familiar
As businesses continue to shift to the cloud, Microsoft Intune has quickly become a key tool for managing devices, policies, and apps. Yet, when setting up Intune, organizations often face a big decision: replicate the tried-and-true on-premises configurations or start fresh with a new cloud-native approach? While recreating existing settings might seem the fastest way to get up and running, starting fresh with Intune is almost always the better choice. Here’s why building from the ground up, rather than relying on legacy setups, makes all the difference in getting the most out of your Intune investment.
1. Avoid Legacy Baggage: Leave Old Issues Behind
On-prem configurations have a way of accumulating “tech debt” over the years—policies created to address specific issues, quick fixes layered on top of each other, and legacy security requirements that may no longer apply. By carrying these old configurations into Intune, you risk dragging along unnecessary complexity, inefficiencies, and even outdated security settings.
Starting fresh with Intune offers the chance to shed that baggage and build a streamlined, efficient configuration that aligns with today’s standards and requirements. By doing this, you’re setting up a cleaner, more manageable environment that’s built for the cloud rather than adapting an outdated setup to fit.
2. Take Full Advantage of Intune’s Cloud-Native Features
One of Intune’s biggest advantages is its cloud-native capabilities. Intune isn’t just a direct replacement for your on-prem tools—it’s designed to offer far more flexibility and agility. By starting fresh, you can make full use of cloud-focused features like:
- Conditional Access: Control access based on location, device health, and more, offering targeted security with far more granularity than typical on-prem setups.
- Windows Autopilot: Enable zero-touch device deployment, getting users up and running from anywhere without complex imaging processes.
- Windows Update for Business: Streamline patching and updates with a cloud-based approach that’s more responsive and less prone to bottlenecks than traditional methods.
These features are tailor-made for a modern, remote-friendly world. If you try to replicate on-prem setups, you’re likely missing out on this flexibility or bending these tools to fit a configuration they weren’t designed for. A fresh start lets you build with these benefits in mind from day one, giving users a seamless experience and admins more control.
3. Simplify Device Enrollment with Intune’s Modern Options
Traditional on-prem deployments often rely on imaging and manual device setups, which are time-consuming and complex. Intune, however, provides a far more streamlined solution through Autopilot. With Autopilot, devices can be shipped directly to users and enrolled automatically, allowing IT teams to configure them remotely.
Starting fresh with Intune lets you avoid trying to shoehorn old enrollment processes into a cloud environment. Instead, you can rethink deployment workflows entirely, reducing overhead and giving users an easy, consistent setup experience no matter where they’re located.
4. Azure AD Join vs. Hybrid Azure AD Join: Embrace Cloud Simplicity

A common question when migrating to Intune is whether to use Azure AD Join or stick with Hybrid Azure AD Join. While Hybrid Join may seem like a safer choice because it retains ties to your on-premises Active Directory, Azure AD Join offers clear advantages in a cloud-first setup.
- Reduced Dependency on On-Premises Infrastructure: Azure AD Join eliminates the need for direct connections to an on-premises domain controller, freeing devices to operate fully in the cloud. This not only reduces the dependency on VPNs but also allows users to work from any location without needing to connect back to the corporate network.
- Simpler, Faster Authentication: Azure AD Join leverages cloud-based authentication, which is often faster and more resilient than relying on an on-premises AD setup. This setup minimizes logon delays for remote users and makes it easier to implement features like passwordless authentication or multi-factor authentication (MFA), enhancing security and improving the overall user experience.
- Supports Conditional Access Policies More Effectively: Azure AD Join is natively designed for integration with Conditional Access policies, allowing for better control and a more granular approach to security. With Azure AD Join, IT teams can enforce policies based on device compliance, user location, or app sensitivity, creating a more flexible and powerful security model.
In short, while Hybrid Azure AD Join offers a bridge to the cloud, Azure AD Join is the optimal choice for businesses ready to move beyond on-prem infrastructure. By fully embracing Azure AD Join, organizations can reduce overhead, simplify management, and position themselves for a truly cloud-first future.
5. Streamline and Optimize Policies
On-prem configurations often become cluttered over time, with layers of policies and configurations built up over years. Trying to transfer these directly to Intune can lead to bloated, redundant, or even conflicting policies that add unnecessary complexity.
Designing your Intune policies from scratch allows you to focus on what’s truly needed today, without the weight of outdated or redundant policies. By reviewing and rethinking policies, you’ll build a leaner, more effective setup that’s easier to manage and quicker to troubleshoot.
6. Enhance Security with Modern, Cloud-Based Controls
Security is an evolving field, and on-prem solutions can sometimes struggle to keep up with the latest threats. With Intune, you can implement Conditional Access policies that adapt based on the security status of each device, giving you more precise control over who can access what data and when. This is difficult to achieve with traditional on-prem setups, which often rely on fixed parameters.
By starting with a clean slate, you can build your security policies around Intune’s dynamic, real-time security features. For example, if you have sensitive data that needs to be accessed only from secure locations or on compliant devices, you can configure policies specifically for that in Intune, enhancing your overall security posture without adding unnecessary restrictions for all users.
7. Improve User Experience and Productivity
One of the biggest advantages of Intune is its ability to support a seamless, mobile-friendly experience. Users today expect access from anywhere, and they don’t want to be bogged down by outdated policies that don’t fit the way they work. Starting fresh with Intune lets you design a user-centric approach, where policies are optimized for mobility, productivity, and flexibility, making work easier and more enjoyable for users while ensuring security.
8. Plan for Future Scalability
Finally, by starting fresh, you’re setting up a foundation that can scale with your organization. Legacy setups often come with limitations and may not be adaptable to new features or requirements as they come out. By creating a tailored, cloud-first Intune strategy, you can easily scale your device management as your organization grows, adding new policies or adjusting configurations without being held back by outdated frameworks.
9. Boost Resiliency with Cloud-First Architecture
A cloud-first approach to Intune, particularly with Azure AD Join, brings significant advantages in terms of resiliency. Unlike on-prem solutions that rely on local servers or VPNs, Intune’s cloud-based architecture minimizes single points of failure. Devices joined to Azure AD don’t need to be tethered to a physical network or a domain controller, meaning that if there’s an outage or connection issue on-site, users can still access critical apps and data from anywhere. Additionally, Microsoft’s global infrastructure ensures that Intune’s services are backed by robust failover and redundancy systems, maximizing uptime. For organizations prioritizing business continuity, this cloud-first resiliency is a game-changer that ensures smooth operations, even during unexpected disruptions.
10. Upgrade Your Network: Ditch the Force-Tunneled VPNs for Direct Access
If you’re modernizing with Intune, it’s time to rethink the network, too. Old-school networks that rely on force-tunneled VPNs (where all traffic is funneled through the corporate data center) can seriously drag down cloud-managed devices. They’re a major bottleneck, slowing everything down and keeping your users from getting the most out of cloud resources. Instead, look into cloud-native direct internet access or SASE (Secure Access Service Edge). These options let devices connect directly to the internet for cloud resources, skipping the clunky VPN route and speeding things up. Modern, managed devices running on a dated network won’t cut it—you need a network that’s ready for the cloud so users can experience the full benefits of Intune without the legacy network hold-ups.
Wrapping It Up: Start Fresh, Think Modern
Designing your Intune strategy from scratch might take a bit of extra time upfront, but it’s an investment that pays off. By avoiding the temptation to replicate old on-prem configurations, you’re embracing a management style built for today’s cloud-first, mobile-centric environment.
So, ditch the legacy baggage, embrace Azure AD Join, and let Intune do what it does best—providing modern, flexible, and efficient device management that meets the needs of your organization now and in the future.
New Look, Same Limitations: Intune’s Company Portal Facelift
September 30, 2024BlogIntune,Company Portal
Microsoft recently gave the Intune Company Portal app for Windows a visual refresh, but while the UI improvements are nice, they don’t solve some of the more pressing issues. If you were hoping for new functionality to make life easier for IT admins, you might be left wanting more. The updated design feels more modern and polished, but the lack of deeper functional updates leaves a few gaps—like the missing "retry" button for required apps and the absence of a quick way to gather logs.
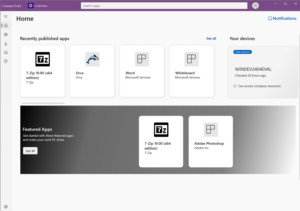
What’s Changed?
The new design for the Company Portal app focuses on improving the user experience through a cleaner interface.
Here’s what’s new:
- Updated Navigation: The navigation pane has been redesigned for easier access to apps, devices, and account settings. It’s sleeker and more intuitive, but the functionality remains largely the same.
- Enhanced Visuals for App Details: App descriptions, version numbers, and installation status are now presented more clearly, offering better readability and a more organized layout.
- UI Consistency Across Platforms: The updated Windows version now aligns more closely with the Company Portal app experience on iOS, Android, and macOS, creating a more unified look across platforms.
What’s Missing?
While the visual overhaul is appreciated, some important features are still absent:
- No "Retry" Button for Required Apps: For IT admins managing required apps, the lack of a "retry" option remains a frustrating oversight. If an app fails to install the first time around, users are left in a bit of a limbo, having to wait for another automatic attempt. A manual "retry" button would provide much-needed control in these situations.
- No Quick Way to Gather Logs: The updated interface still doesn’t include a fast, user-friendly way to collect logs for troubleshooting. Gathering logs is a crucial step for IT teams when diagnosing issues, and a quick method to do this directly within the Company Portal would save significant time and effort, especially when resolving support tickets.
- Better Application detection: If you've ever tried uninstalling an app through the Company Portal, you've probably encountered the issue where the uninstall button doesn’t show up right away or an app that has already been isntalled, has not been detected.It would be great to see improvements with detecting app statuses in real-time. While a fresh look is great, fixing these basic functionality issues would have been a much more impactful update.
Why This Matters
The updates to the Company Portal make the app look better, but for IT admins and organizations managing large device fleets, the functionality is what really matters. Without the ability to easily retry failed app installations or collect logs, the frustrations of managing devices remain.
Sure, the cleaner UI is a welcome change, but it’s the absence of deeper tools—like better error handling for app installs and streamlined troubleshooting—that keeps this update from being as impactful as it could be.
Wrapping It Up
Microsoft’s redesign of the Intune Company Portal app feels like a step in the right direction, but it’s mostly about looks. The missing "retry" button for required apps and the lack of a quick way to gather logs are still glaring omissions that make device management harder than it needs to be.
So while the fresh look is nice, it’s still a case of form over function. Hopefully, future updates will bring the essential tools that admins and users need to make their lives easier. Until then, it’s all about appreciating the superficial improvements while managing the same old challenges.