Windows 10 Is Out, Windows 11 Is In: Why It’s Time to Upgrade
The clock is ticking for Windows 10. Microsoft has officially marked October 14, 2025, as the end-of-life date for the beloved OS. That might sound like a distant deadline, but in IT terms, it’s right around the corner. If your organization hasn’t started planning for Windows 11, now’s the time to get moving.
Let’s talk about what end-of-life means, why you can’t ignore it, and how to make the jump to Windows 11 without losing your mind (or your weekends).
What Does End-of-Life Mean for Windows 10?
When Windows 10 hits its expiration date, here’s what you’ll lose:
- No more security updates: Vulnerabilities won’t get patched, leaving your systems exposed.
- No feature updates: Windows 10 will stagnate while the rest of the tech world moves forward.
- No official support: You’re on your own for troubleshooting and compliance issues.
Running an unsupported OS isn’t just risky—it’s a compliance and security nightmare. For most businesses, staying on Windows 10 past 2025 simply isn’t an option.
Why Upgrade to Windows 11?
Windows 11 isn’t just a cosmetic refresh. It’s built for the modern workplace, focusing on security, productivity, and future-proofing. Here’s why it’s worth the move:
- Zero Trust Security: Features like TPM 2.0, Virtualization-Based Security (VBS), and hardware root-of-trust support make it a fortress for modern threats.
- Productivity Enhancements: Snap Layouts, better multi-monitor support, and Teams integration help users work smarter, not harder.
- Hybrid Work Ready: Optimized for cloud environments, Windows 11 is built with hybrid and remote work in mind.
- Long-Term Support: Sticking with Windows 10 means falling further behind, while Windows 11 positions your organization for what’s next.
Planning Your Windows 11 Upgrade
The move to Windows 11 doesn’t have to be chaotic. Here’s a step-by-step approach to keep things smooth:
1. Assess Your Hardware
Windows 11 has stricter requirements than its predecessor (hello, TPM 2.0). Start by auditing your current hardware to see what’s compatible.
Use Intune for a Hardware Assessment
- Navigate to Endpoint Analytics in Intune.
- Check the Work From Anywhere report to identify devices that are Windows 11 ready.
Tip: Devices that don’t meet the requirements may need upgrading or replacing—start budgeting early.
2. Test the New OS
Don’t roll out Windows 11 to everyone at once. Test it with a small group of users first (preferably IT and power users). Use their feedback to refine your deployment strategy.
3. Leverage Intune for Deployment
If you’re managing your environment with Intune, upgrading to Windows 11 is straightforward. Use Windows Update for Business to deploy feature updates in a controlled manner:
- Go to Devices > Windows > Feature Updates.
- Create a new policy targeting Windows 11 24H2 or the latest version.
- Assign the policy to Azure AD groups.
Pro Tip: Use Update Rings to stagger the rollout and test updates before pushing them to all users.
4. Train Your Users
Even minor interface changes can confuse users. Prepare your teams with:
- Short training sessions on Windows 11’s new features.
- Guides or videos highlighting productivity boosters like Snap Layouts and Teams integration.
Overcoming Common Objections
Some users (or even IT admins) might resist the change. Here’s how to address the usual pushback:
- “We need to test everything before upgrading.”
Sure, but Windows 11 is part of an evergreen model—updates will keep coming. Adopt a test-and-deploy mindset instead of waiting for “perfect.” - “Our hardware isn’t ready.”
Start identifying devices that need replacing now. You’ve got time, but don’t leave it too late. - “We can’t afford downtime.”
Use Intune’s zero-touch deployment capabilities and tools like Windows Autopilot to minimize disruption.
Why Procrastination Is a Bad Idea
October 2025 might seem far away, but large-scale migrations take time. If you wait until 2025 to start planning, you’ll be scrambling to meet the deadline. Here’s why early action is critical:
- Avoid the rush: As the deadline approaches, vendors and support teams will be swamped.
- Stay secure: Upgrading sooner means fewer months spent on an unsupported OS.
- Get ahead of the curve: Windows 11’s modern tools and features can drive productivity gains right now.
Final Thoughts
The end of Windows 10 isn’t just a deadline—it’s an opportunity. Moving to Windows 11 brings better security, improved productivity, and a platform built for the future of work. With tools like Intune and Windows Autopilot, the upgrade process can be streamlined and efficient.
So, don’t wait. Start planning your move today, and by the time October 2025 rolls around, you’ll already be reaping the benefits of Windows 11.
Ready to Get Started?
Let me know how I can help you make your Windows 11 upgrade seamless and stress-free!
Intune Done Right: Business Change or Bust!
Adopting modern management tools like Intune, Azure AD, and other MDM solutions is a strategic move for any enterprise aiming to boost flexibility, security, and efficiency. But here’s the hard truth: rolling out these tools without a business change strategy is a recipe for failure. For medium and large organizations especially, aligning processes, people, and strategy with modern management is critical. Without it, you risk poor adoption, endless troubleshooting, and missed opportunities—especially in an evergreen IT environment where Windows, applications, and security policies are constantly evolving. Here’s why business change is non-negotiable for a successful modern management rollout in any enterprise.
1. Modern Management Requires Enterprise-Wide Process Changes
Modern management tools are agile, cloud-based, and highly adaptable, but they require different workflows than traditional on-prem setups. Moving from Active Directory and SCCM to a cloud-centric approach means changing how teams work and how IT supports the business. Without adjusting enterprise processes, you’re slapping modern tools onto an outdated system, leading to mismatched policies, broken workflows, and frustration for both IT and end-users.
Key Insight: Align business change processes with the mobile, flexible nature of modern management, making it easier for departments across the enterprise to adopt the new system smoothly.
2. Evergreen IT Demands Continuous Change—and Enterprises Must Be Ready
Modern management in a large enterprise isn’t just a one-time deployment; it’s a continuously evolving approach. With evergreen IT, regular updates roll out across tools, OS versions, and applications, meaning your entire organization must adapt without significant disruption. A lack of business change strategy leaves each update feeling like a shock rather than a smooth transition, causing disruption for users and backlogs for IT.
One major shift is the continuous updates in Windows and business applications. Gone are the days when organizations could delay updates indefinitely to allow time for extensive testing. With Windows updating regularly, business-as-usual (BAU) applications must be updated to stay compatible, raising the question: who’s managing that work?
The days of waiting for IT to test every patch before rollout are over, and businesses need to adjust. Without clear ownership of application updates, your organization could face compatibility issues, security risks, and degraded user experiences.
Key Insight: Embrace a mindset of continuous improvement, treating each update as a strategic opportunity for refinement rather than a hurdle. For large organizations, this approach minimizes user downtime and keeps systems performing at peak.
3. End-User Training and Communication Are Non-Negotiable
Rolling out modern management tools to thousands of users without a clear training and communication plan is a recipe for failure. Large organizations need structured, consistent training programs to help users understand new interfaces, settings, and behaviors.
Without this, confusion reigns—user productivity drops, support calls rise, and adoption lags.
Key Insight: Design a training and communication strategy that scales across teams and departments, empowering employees with the skills they need to maximize productivity.
4. Security is Dynamic—So Should Be Your Enterprise Policies
Modern management often means implementing dynamic security policies—conditional access, compliance checks, and real-time threat detection.
However, these tools are only as effective as the processes that govern them. Large enterprises, with their complex security requirements, need security policies that are adaptable and enforceable across varied departments and geographies.
Relying on static security policies tied to on-prem practices limits the benefits of dynamic cloud tools.
Key Insight: Develop adaptive security policies that can scale and respond quickly to emerging threats across your entire organization, ensuring each department stays secure without losing productivity.
5. IT and Support Teams Need to Evolve Alongside the Technology
For large enterprises, modern management doesn’t just change device management—it reshapes the whole IT support model.
Legacy setups often include centrally managed, on-prem solutions that differ vastly from cloud-based support and remote troubleshooting required by modern management. Without upskilling and evolving the support team, your enterprise risks service delays, inconsistent issue resolution, and missed opportunities to proactively manage the environment.
Key Insight: Invest in IT and support training to ensure teams are skilled in cloud management, remote troubleshooting, and proactive monitoring. This prepares your IT team for the challenges of large-scale modern management.
6. The Culture Shift: Empowering Users While Maintaining Control
One of the biggest challenges for medium and large enterprises is balancing user empowerment with control.
Modern management encourages a flexible, user-centric approach, but without the right cultural shift, users may find themselves confused by new expectations or bypassing policies altogether.
Large organizations, with their diverse teams and departmental needs, must create a culture that supports user independence while enforcing security and compliance.
Key Insight: Establish a culture of trust and accountability, making it clear that while users have greater flexibility, security remains paramount.
7. Prevent Fragmentation and Shadow IT
In large enterprises, the temptation to rely on unapproved tools grows when official systems aren’t meeting user needs.
A lack of business alignment in modern management can result in fragmentation and shadow IT, where departments find their own solutions to work around limitations. This not only compromises security but also creates data silos and increases IT complexity.
Key Insight: Engage department heads and team leads in the rollout process to ensure the tools and processes meet diverse needs, keeping teams unified and reducing shadow IT.
Wrapping Up: Modern Management Without Business Change is a Missed Opportunity
For medium and large enterprises, implementing modern management without business alignment is like upgrading to a high-performance engine without adjusting the rest of the car—it’s bound to underperform.
In an evergreen IT world, where change is constant, your organization must be ready to adapt seamlessly.
With a strong business change strategy, you’re not just adopting new tools; you’re building a resilient, user-centered, and flexible IT framework ready to meet the demands of a modern, dynamic enterprise.
Windows 365 Link: Cloud PC Just Got Real
We’re all used to the idea of a PC being a device—your laptop, your desktop, maybe even a fancy all-in-one. But what if your "PC" wasn’t really a PC at all? Enter the Windows 365 Link, Microsoft’s compact bridge between you and the cloud. It’s not here to replace your hardware entirely, but to rethink how we use it.
The Link is designed to connect directly to your Windows 365 Cloud PC, making your workspace portable, secure, and—most importantly—not tied to a traditional endpoint. Let’s break down what this means for how we work and why it might be a big deal for businesses. It’s a rethink of how we approach security, management, and productivity. It also closes the missing gap that was present in the W365 ecosystem.

No Physical Attack Surface, No Problem
One of the Link’s standout features is its complete lack of local storage. No files, no apps, no admin accounts. At first, that might seem limiting, but here’s the genius: there’s nothing on the device for attackers to exploit. If the Link is stolen, it’s just a tiny paperweight for anyone who doesn’t have access to your Cloud PC.
For businesses handling sensitive data, like finance or healthcare, this is a game-changer. Local machines are always at risk of being breached or compromised. The Link removes that risk entirely by keeping everything in the cloud. It’s like a secure tunnel that ensures your data is always protected, no matter where you are.
- Physical theft: Lose a laptop, and your data could end up anywhere. Lose the Link? There’s nothing stored locally for attackers to exploit.
- Malware attacks: The locked-down OS prevents unauthorized software from running or installing locally, drastically reducing the risk of breaches.
- Privileged escalations: No local admin accounts mean attackers can’t exploit traditional elevation-of-privilege attacks to gain control.
For industries that deal with sensitive information—finance, healthcare, or government—the reduced attack surface makes the Windows 365 Link an obvious choice.
Built for Privileged Access Workstations (PAWs)
If you’ve ever tried to implement Privileged Access Workstations (PAWs), you know they’re a hassle. These specialized devices are designed for highly secure tasks—think system administration or managing sensitive data—but they’re costly and complex to set up. The Windows 365 Link changes that.
With no local data and built-in support for FIDO2 security keys, the Link makes securing privileged access much simpler. Passwordless, hardware-backed authentication means no weak passwords to exploit, and no need for bulky, high-spec machines just for security’s sake. At $349, it’s a cost-effective way to deploy secure workstations without sacrificing functionality. For IT admins, it’s a quick win that checks all the compliance boxes without breaking the budget.
- Secure by design: With no local admin accounts or storage, the Link aligns perfectly with the zero-trust principles of PAWs.
- Enhanced authentication: The device supports FIDO2 security keys, enabling passwordless, hardware-backed authentication for privileged users. This reduces the risk of phishing attacks and ensures only authorized personnel can access sensitive systems.
- Cost-effective: At $349, it’s significantly cheaper than building out dedicated, high-end PAW setups while offering superior security through cloud-native management.
Built for Hybrid Work
Perfect for the Hybrid Work Era
Hybrid work isn’t a trend anymore—it’s the way we work now. But with hybrid setups come challenges: laptops lugged between home and office, forgotten chargers, and inconsistent environments. The Link offers a simple solution.

It’s small, portable, and packed with modern connectivity. Dual 4K monitor support, Wi-Fi 6E, Bluetooth 5.3, and Ethernet mean it’s ready for just about any setup. Plug it into a monitor and peripherals, and you’re instantly connected to your Cloud PC. No need to sync files or carry around a full device.
This isn’t just handy for hybrid workers—it’s perfect for hot-desking environments, too. Instead of provisioning expensive laptops for every desk, you just provide a Link. Simple, scalable, and far less hassle for IT.
- Dual 4K monitor support for high-productivity setups.
- Wi-Fi 6E, Bluetooth 5.3, and Ethernet connectivity to ensure compatibility with any network.
- Plug-and-play simplicity that turns any screen into a secure workstation connected to your Cloud PC.
IT Management Without the Drama
If you’re an IT admin, you’ve probably rolled your eyes at “revolutionary” devices that make big promises but add complexity to your workload. The Link is different because it’s built to integrate seamlessly into the tools you’re already using, like Microsoft Intune.
From zero-touch provisioning to automatic updates, managing the Link is as straightforward as managing a traditional endpoint. Policies? Same as any other device. Updates? They’re applied in the background overnight. It’s an endpoint that fits neatly into your existing processes without reinventing the wheel.
And because it’s entirely cloud-driven, there’s no need to worry about patching local vulnerabilities, maintaining a separate device inventory for physical machines or even having these on your internal facing LAN. It just works.
Why It Matters
The Windows 365 Link might look like a small, unassuming device, but it’s tackling some big problems. It removes local vulnerabilities, simplifies endpoint management, and makes hybrid work more efficient. For businesses already using Windows 365, it’s an obvious next step. For those on the fence about cloud PCs, it might just be the nudge they need.
This isn’t about replacing every device in your organization, but about rethinking how and where you work. The Link isn’t flashy, and it doesn’t need to be. It’s about utility—making your workspace more secure, more portable, and less of a headache for everyone involved.
Final Thoughts
The Windows 365 Link isn’t going to revolutionize how you work overnight. But it’s a clear step toward a world where your "PC" isn’t tied to a physical machine. It’s secure, simple, and built for modern work.
If you’re managing hybrid teams, privileged users, or just looking to simplify your endpoint strategy, this little device is worth a closer look. It’s not the whole solution, but it might just be the most practical piece of the puzzle you’ve been missing.
Intune Done Right: Why Fresh Beats Familiar
As businesses continue to shift to the cloud, Microsoft Intune has quickly become a key tool for managing devices, policies, and apps. Yet, when setting up Intune, organizations often face a big decision: replicate the tried-and-true on-premises configurations or start fresh with a new cloud-native approach? While recreating existing settings might seem the fastest way to get up and running, starting fresh with Intune is almost always the better choice. Here’s why building from the ground up, rather than relying on legacy setups, makes all the difference in getting the most out of your Intune investment.
1. Avoid Legacy Baggage: Leave Old Issues Behind
On-prem configurations have a way of accumulating “tech debt” over the years—policies created to address specific issues, quick fixes layered on top of each other, and legacy security requirements that may no longer apply. By carrying these old configurations into Intune, you risk dragging along unnecessary complexity, inefficiencies, and even outdated security settings.
Starting fresh with Intune offers the chance to shed that baggage and build a streamlined, efficient configuration that aligns with today’s standards and requirements. By doing this, you’re setting up a cleaner, more manageable environment that’s built for the cloud rather than adapting an outdated setup to fit.
2. Take Full Advantage of Intune’s Cloud-Native Features
One of Intune’s biggest advantages is its cloud-native capabilities. Intune isn’t just a direct replacement for your on-prem tools—it’s designed to offer far more flexibility and agility. By starting fresh, you can make full use of cloud-focused features like:
- Conditional Access: Control access based on location, device health, and more, offering targeted security with far more granularity than typical on-prem setups.
- Windows Autopilot: Enable zero-touch device deployment, getting users up and running from anywhere without complex imaging processes.
- Windows Update for Business: Streamline patching and updates with a cloud-based approach that’s more responsive and less prone to bottlenecks than traditional methods.
These features are tailor-made for a modern, remote-friendly world. If you try to replicate on-prem setups, you’re likely missing out on this flexibility or bending these tools to fit a configuration they weren’t designed for. A fresh start lets you build with these benefits in mind from day one, giving users a seamless experience and admins more control.
3. Simplify Device Enrollment with Intune’s Modern Options
Traditional on-prem deployments often rely on imaging and manual device setups, which are time-consuming and complex. Intune, however, provides a far more streamlined solution through Autopilot. With Autopilot, devices can be shipped directly to users and enrolled automatically, allowing IT teams to configure them remotely.
Starting fresh with Intune lets you avoid trying to shoehorn old enrollment processes into a cloud environment. Instead, you can rethink deployment workflows entirely, reducing overhead and giving users an easy, consistent setup experience no matter where they’re located.
4. Azure AD Join vs. Hybrid Azure AD Join: Embrace Cloud Simplicity

A common question when migrating to Intune is whether to use Azure AD Join or stick with Hybrid Azure AD Join. While Hybrid Join may seem like a safer choice because it retains ties to your on-premises Active Directory, Azure AD Join offers clear advantages in a cloud-first setup.
- Reduced Dependency on On-Premises Infrastructure: Azure AD Join eliminates the need for direct connections to an on-premises domain controller, freeing devices to operate fully in the cloud. This not only reduces the dependency on VPNs but also allows users to work from any location without needing to connect back to the corporate network.
- Simpler, Faster Authentication: Azure AD Join leverages cloud-based authentication, which is often faster and more resilient than relying on an on-premises AD setup. This setup minimizes logon delays for remote users and makes it easier to implement features like passwordless authentication or multi-factor authentication (MFA), enhancing security and improving the overall user experience.
- Supports Conditional Access Policies More Effectively: Azure AD Join is natively designed for integration with Conditional Access policies, allowing for better control and a more granular approach to security. With Azure AD Join, IT teams can enforce policies based on device compliance, user location, or app sensitivity, creating a more flexible and powerful security model.
In short, while Hybrid Azure AD Join offers a bridge to the cloud, Azure AD Join is the optimal choice for businesses ready to move beyond on-prem infrastructure. By fully embracing Azure AD Join, organizations can reduce overhead, simplify management, and position themselves for a truly cloud-first future.
5. Streamline and Optimize Policies
On-prem configurations often become cluttered over time, with layers of policies and configurations built up over years. Trying to transfer these directly to Intune can lead to bloated, redundant, or even conflicting policies that add unnecessary complexity.
Designing your Intune policies from scratch allows you to focus on what’s truly needed today, without the weight of outdated or redundant policies. By reviewing and rethinking policies, you’ll build a leaner, more effective setup that’s easier to manage and quicker to troubleshoot.
6. Enhance Security with Modern, Cloud-Based Controls
Security is an evolving field, and on-prem solutions can sometimes struggle to keep up with the latest threats. With Intune, you can implement Conditional Access policies that adapt based on the security status of each device, giving you more precise control over who can access what data and when. This is difficult to achieve with traditional on-prem setups, which often rely on fixed parameters.
By starting with a clean slate, you can build your security policies around Intune’s dynamic, real-time security features. For example, if you have sensitive data that needs to be accessed only from secure locations or on compliant devices, you can configure policies specifically for that in Intune, enhancing your overall security posture without adding unnecessary restrictions for all users.
7. Improve User Experience and Productivity
One of the biggest advantages of Intune is its ability to support a seamless, mobile-friendly experience. Users today expect access from anywhere, and they don’t want to be bogged down by outdated policies that don’t fit the way they work. Starting fresh with Intune lets you design a user-centric approach, where policies are optimized for mobility, productivity, and flexibility, making work easier and more enjoyable for users while ensuring security.
8. Plan for Future Scalability
Finally, by starting fresh, you’re setting up a foundation that can scale with your organization. Legacy setups often come with limitations and may not be adaptable to new features or requirements as they come out. By creating a tailored, cloud-first Intune strategy, you can easily scale your device management as your organization grows, adding new policies or adjusting configurations without being held back by outdated frameworks.
9. Boost Resiliency with Cloud-First Architecture
A cloud-first approach to Intune, particularly with Azure AD Join, brings significant advantages in terms of resiliency. Unlike on-prem solutions that rely on local servers or VPNs, Intune’s cloud-based architecture minimizes single points of failure. Devices joined to Azure AD don’t need to be tethered to a physical network or a domain controller, meaning that if there’s an outage or connection issue on-site, users can still access critical apps and data from anywhere. Additionally, Microsoft’s global infrastructure ensures that Intune’s services are backed by robust failover and redundancy systems, maximizing uptime. For organizations prioritizing business continuity, this cloud-first resiliency is a game-changer that ensures smooth operations, even during unexpected disruptions.
10. Upgrade Your Network: Ditch the Force-Tunneled VPNs for Direct Access
If you’re modernizing with Intune, it’s time to rethink the network, too. Old-school networks that rely on force-tunneled VPNs (where all traffic is funneled through the corporate data center) can seriously drag down cloud-managed devices. They’re a major bottleneck, slowing everything down and keeping your users from getting the most out of cloud resources. Instead, look into cloud-native direct internet access or SASE (Secure Access Service Edge). These options let devices connect directly to the internet for cloud resources, skipping the clunky VPN route and speeding things up. Modern, managed devices running on a dated network won’t cut it—you need a network that’s ready for the cloud so users can experience the full benefits of Intune without the legacy network hold-ups.
Wrapping It Up: Start Fresh, Think Modern
Designing your Intune strategy from scratch might take a bit of extra time upfront, but it’s an investment that pays off. By avoiding the temptation to replicate old on-prem configurations, you’re embracing a management style built for today’s cloud-first, mobile-centric environment.
So, ditch the legacy baggage, embrace Azure AD Join, and let Intune do what it does best—providing modern, flexible, and efficient device management that meets the needs of your organization now and in the future.
New Look, Same Limitations: Intune’s Company Portal Facelift
Microsoft recently gave the Intune Company Portal app for Windows a visual refresh, but while the UI improvements are nice, they don’t solve some of the more pressing issues. If you were hoping for new functionality to make life easier for IT admins, you might be left wanting more. The updated design feels more modern and polished, but the lack of deeper functional updates leaves a few gaps—like the missing "retry" button for required apps and the absence of a quick way to gather logs.
What’s Changed?
The new design for the Company Portal app focuses on improving the user experience through a cleaner interface.
Here’s what’s new:
- Updated Navigation: The navigation pane has been redesigned for easier access to apps, devices, and account settings. It’s sleeker and more intuitive, but the functionality remains largely the same.
- Enhanced Visuals for App Details: App descriptions, version numbers, and installation status are now presented more clearly, offering better readability and a more organized layout.
- UI Consistency Across Platforms: The updated Windows version now aligns more closely with the Company Portal app experience on iOS, Android, and macOS, creating a more unified look across platforms.
What’s Missing?
While the visual overhaul is appreciated, some important features are still absent:
- No "Retry" Button for Required Apps: For IT admins managing required apps, the lack of a "retry" option remains a frustrating oversight. If an app fails to install the first time around, users are left in a bit of a limbo, having to wait for another automatic attempt. A manual "retry" button would provide much-needed control in these situations.
- No Quick Way to Gather Logs: The updated interface still doesn’t include a fast, user-friendly way to collect logs for troubleshooting. Gathering logs is a crucial step for IT teams when diagnosing issues, and a quick method to do this directly within the Company Portal would save significant time and effort, especially when resolving support tickets.
- Better Application detection: If you've ever tried uninstalling an app through the Company Portal, you've probably encountered the issue where the uninstall button doesn’t show up right away or an app that has already been isntalled, has not been detected.It would be great to see improvements with detecting app statuses in real-time. While a fresh look is great, fixing these basic functionality issues would have been a much more impactful update.
Why This Matters
The updates to the Company Portal make the app look better, but for IT admins and organizations managing large device fleets, the functionality is what really matters. Without the ability to easily retry failed app installations or collect logs, the frustrations of managing devices remain.
Sure, the cleaner UI is a welcome change, but it’s the absence of deeper tools—like better error handling for app installs and streamlined troubleshooting—that keeps this update from being as impactful as it could be.
Wrapping It Up
Microsoft’s redesign of the Intune Company Portal app feels like a step in the right direction, but it’s mostly about looks. The missing "retry" button for required apps and the lack of a quick way to gather logs are still glaring omissions that make device management harder than it needs to be.
So while the fresh look is nice, it’s still a case of form over function. Hopefully, future updates will bring the essential tools that admins and users need to make their lives easier. Until then, it’s all about appreciating the superficial improvements while managing the same old challenges.
WSUS is Out—What’s Next? Microsoft’s Shift to Modern Update Management
WSUS, the trusty tool many of us have relied on for patch management, is officially heading for the exit. https://techcommunity.microsoft.com/t5/windows-it-pro-blog/windows-server-update-services-wsus-deprecation/ba-p/4250436
With Microsoft’s announcement of WSUS deprecation, the question looms: “What’s next for update management?” Don’t worry—there’s a cloud-friendly future waiting. Let’s break down what this means, when it’s happening, and how you can stay ahead of the curve.
Why is WSUS Being Deprecated?
After more than two decades of faithfully distributing patches, WSUS is finally being phased out. The tool was a staple in on-premises environments, offering IT admins granular control over which updates were deployed and when. However, with the shift to cloud-based infrastructures, Microsoft is steering towards more modern, scalable, and flexible solutions.
Simply put, WSUS is being retired because it wasn’t designed for today’s hybrid and cloud-first environments. The modern workplace demands seamless updates across diverse device fleets, from on-prem servers to remote laptops. Enter Microsoft Endpoint Manager, Intune, and Windows Update for Business, the cloud-driven solutions poised to take over WSUS’s role.
When Will WSUS Be Deprecated?
Microsoft has outlined a gradual deprecation process, which means you won’t wake up tomorrow to find WSUS suddenly gone. Instead, the timeline allows for a smooth transition:
•Active Deprecation: With each new release of Windows Server, you’ll see more features of WSUS being retired.
•Support Ends with Server 2025: Official support for WSUS is set to end by 2025, giving organizations time to transition.
This gives IT pros plenty of runway to adjust their update strategies. However, it’s best not to wait until the last minute to explore alternatives.
What’s Next? The Modern Alternatives
Now that WSUS is heading into the sunset or bin, Microsoft has made it clear where the future lies—Microsoft Intune. This cloud-based platform, combined with Windows Update for Business, is your ticket to managing updates across hybrid environments.
•Microsoft Intune: As part of Microsoft Endpoint Manager, Intune lets you manage updates and policies from a central hub, whether devices are on-premises or remote. The flexibility to manage Windows, macOS, iOS, and Android from a single console is a game-changer.
•Windows Update for Business (WUfB): Integrated within Intune, WUfB allows you to automate update deployment directly from Microsoft’s cloud services. It offers more streamlined management of Windows updates without the need for the infrastructure WSUS required. Plus, WUfB is built for the modern era—it scales as your device fleet grows and adapts to the needs of a hybrid workforce.
Granularity: WSUS vs. WUfB
One thing to note is that WUfB is less granular compared to WSUS. With WSUS, admins had precise control over individual updates, allowing them to pick and choose which patches were deployed and when. In contrast, WUfB embraces an “evergreen” approach, which focuses on keeping devices automatically updated with the latest features and security patches. While this ensures devices stay current and secure, it offers less flexibility for those who prefer to selectively approve updates or hold back specific upgrades. However, for many organisation, the benefits of an evergreen environment far outweigh the need for micromanaging individual updates. Let's face it, the evergreen approach is here to stay.
If your organisation requires more granular control over updates—similar to what WSUS provided—then third-party patch management tools may be the way to go. While Windows Update for Business (WUfB) offers a more streamlined, cloud-friendly approach, it lacks the ability to pick and choose individual updates with the same level of detail. For businesses that need to carefully manage which patches are deployed or need to hold back specific updates for testing, third-party tools offer the flexibility and granular control that WUfB doesn’t. These tools can handle Windows updates, as well as patches for third-party applications, giving you a more tailored approach to update management without sacrificing control, however this needs to be balanced against the cost of essentially paying twice for the same service.
How to Prepare for the WSUS Transition
Transitioning away from WSUS may seem daunting, but here are a few steps to make the process smoother:
1. Audit Your Current Setup: Start by taking stock of your WSUS deployment and assess how it fits into your broader IT strategy.
2. Evaluate Microsoft Intune: If you’re not already using Intune, this is the perfect time to explore how it can streamline your device management and update strategy.
3. Plan for Migration: Create a roadmap for migrating from WSUS to Intune, ensuring you have the resources and time to test, train, and fully transition your IT team.
The Future is Cloudy (and That’s a Good Thing)
While WSUS has been a reliable workhorse, the future of IT update management is all about the cloud. With Intune and Windows Update for Business, you’ll have the flexibility, scalability, and security needed to thrive in a modern, hybrid world. So, wave goodbye to WSUS and say hello to a more agile, efficient way of managing updates.
Windows Enrollment Just Got a Glow-Up: Here’s the Good, the Bad, and the Patchy
Starting October 2024, new Windows 11 devices (version 22H2+) will automatically download and install quality updates during the Out-of-Box Experience (OOBE) when enrolled via MDM like Intune. This ensures devices are secure before user login.
Advantages:
- Better Security: Immediate patching reduces risks from out-of-date software.
- Compliance: Ensures policies are met from day one.
Disadvantages:
- Longer Enrollment: Updates during OOBE might delay device handoff.
- Access Pass Adjustments: Temporary Access Passes may expire before setup is complete.
- Updates whether you want them or not: No more choice in the process.
Final Thoughts:
While the enhanced security is a significant benefit, the extended setup time could become a challenge for organizations with tight provisioning schedules. Admins managing large fleets may need to plan for the additional time required for these updates. The Temporary Access Pass issue also means careful coordination will be needed, particularly in environments relying on quick deployments or where devices are being "White Gloved" on behalf of Assistive Technology users.
For businesses prioritizing immediate security and compliance, this update is a step in the right direction. However, organizations focused on speed or with existing streamlined processes may face slight disruptions. Balancing security with efficiency will be key. One thing is for sure, Microsoft is keen for you to be on the latest updates!
Autopilot 2.0: Microsoft’s Slick New Rollout for Gov & Enterprise!
Microsoft has dropped a fresh upgrade for Windows Autopilot, and it's a game changer, especially for IT admins in government and large enterprises. The new features streamline the onboarding process, improve error handling, and provide support for government clouds like GCC High and DoD. If you're dealing with large-scale deployments, this update just made things smoother and less of a headache.
Key Features You’ll Love:
- Improved Out-of-Box Experience (OOBE): You can now see real-time progress as devices are onboarded. This not only gives you peace of mind but also lets you track issues before users get their hands on the device. The new UI is cleaner and provides more insight into the deployment process, which helps IT teams pinpoint problems quickly.
- Stronger Error Handling: The update includes enhanced error resiliency, meaning that even if something goes wrong during the setup, the system can handle it better, reducing the number of failed deployments. This saves time and frustration, especially in large environments where downtime can be costly.
- Government Cloud Support: For those managing sensitive environments, Autopilot now has extended support for government clouds, including GCC High and DoD. This means that government institutions with high security requirements can now enjoy the benefits of Autopilot without compromising on compliance or control.
 Why It Matters:
Why It Matters:
The latest Autopilot updates are tailored for large-scale deployments, making it easier to manage thousands of devices while ensuring they stay secure and up-to-date. With better visibility into the onboarding process and a stronger focus on error resilience, IT departments can spend less time troubleshooting and more time focusing on strategic tasks.
For government bodies and enterprises that require strict security and compliance, these features are a blessing. The ability to deploy devices into secure environments like GCC High and DoD clouds without extra steps means faster, more efficient rollouts.
What’s the Catch?
While the updates bring a lot of improvements, it’s worth noting that device setup may still take some time, especially with larger batches. But overall, these enhancements mean fewer bumps along the way, less downtime, and a more intuitive deployment process.
Final Thoughts:
This Autopilot update is all about saving time, reducing errors, and providing greater control for IT admins working with large or highly secure environments. If you’re an IT admin in government or enterprise, these changes are worth exploring. Not only will they improve how you manage devices, but they’ll also give you more confidence in the deployment process from start to finish.
For more details, check out the full announcement here.
Intune Autopilot – Part 2 – Moving in the right direction!
Cont.
So if you've read part one, then you're looking for a way to set up an Intune managed Autopilot device to be shared among multiple users.
The chances are that you're already using autopilot for your single-user devices. Which means that you already have an Azure AD Dynamic Group, probably using a dynamic query such as:
(device.devicePhysicalIDs -any (_ -contains "[ZTDId]"))
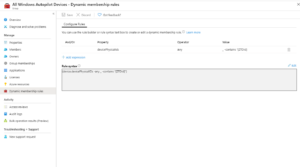
The problem with this approach is that it's going to lump all of our autopilot devices into one AAD Dynamic group, which is no good if we need multiple deployment profiles (User Driven + Self-Deploying profiles). So we need a way to separate these devices. Enter the OrderID field...
The OrderID field, also referred to as GroupTag will allow us to create different groups of Autopilot devices, so that we can deploy Single User laptops, Shared PCs, and Kiosk devices all with different profiles and policy sets. However, if we are using the ZTDId tag, the chances are that none of our existing computers has the order IT field populated.
Therefore we need to populate the OrderID value for all existing devices and change our Dynamic AD groups to match the OrderID, not all autopilot devices.
Thankfully, Nicola Suter has come to the rescue here. He has written a PowerShell script that will connect to Graph API, and allow us to change the OrderID field in bulk. https://tech.nicolonsky.ch/bulk-update-windows-autopilot/ In this example. I'm going to use a group tag of "autopilot" to signify a standard user-driven deployed device, therefore we will use Nicola's scripts to change the group tag to "Autopilot" on all existing devices.
In conjunction, with this, we also need to change the Dynamic group query in Azure AD from targeting ZTDid to something like this:
(device.devicePhysicalIds -any _ -eq “[OrderID]:Value”)
Where "Value" is the value, you want to put in the OrderID field.
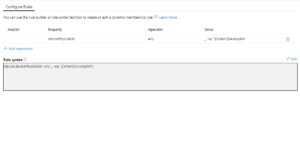
Once we have done this, we can start building a new policy and profile set for our other devices. In part 3, we will explore a multi-user desktop and kiosk mode deployment alongside traditional user-driven deployments.
Intune Autopilot - Sharing the love - Part 1
Over the last 18 months, I've had great success deploying modern-managed devices for clients, using a mix of Azure Active Directory, Intune and Autopilot. Autopilot has always worked great in scenarios where one user = one workstation, but what about a replacement for that traditional domain-joined PC which you would deploy for shift workers or in multi-user situations where one computer = 5 users?
There are a few ways that I have found a multi-user device can be set-up, but these all have drawbacks.
Build a PC then AAD join it:
On the face of it, this seems like the most straightforward option. The PC can be AAD joined and added into AAD Device groups to receive policies. However, the drawback with this approach is that the machine will be listed in AAD as a device under the user that AAD joined it. This can lead to admin accounts with tens of devices listed under them and a potential requirement to lift the "per user device limit" within AAD.
It's also a royal pain in the backside to have to assign group memberships manually, and policy application appears to be a little spotty the moment you transition to a standard user.
SharedPC CSP
Microsoft has thought of this and created a SharedPC CSP policy. SharedPC CSP comes with several advantages such as Guest account Management, Local Storage Policies, Power Policies, Fast first sign-in and Education Policies, all of which make management and sign-in much easier. But for me, this CSP has one critical flaw - it disables the OneDrive client completely!!
If like me, you've been encouraging people to take advantage included 1TB OneDrive space per user in Office 365, then you've probably migrated users' documents to OneDrive and are using policies such as KFM (known folder move). OneDrive client is critical to a Shared PC; otherwise, users will are forced to use OneDrive online to access their documents. It also gives no easy way to roam documents between shared PCs, for example at a reception desk with two seats.

So, how do we deploy an Intune Autopilot device for multiple users with all of our usual Line of Business apps?
The answer is Intune Self-Deploying Mode but without SharedPC CSP!!
What, I hear you cry, that sounds counter-intuitive, but it works. We'll let the self-deploying mode take care of our AAD join and then layer some custom Policies on top to cover the other bits.
The self-deploying mode requires adding another Autopilot deployment profile, which means you must make some changes to your existing autopilot configuration. In Part 2, I'll go into the changes that you need to make to prepare your environment for multiple deployment profiles.